Encryption
We use OpenPGP.js to secure your communication. It’s based on the OpenPGP standard which came from the proprietary product PGP (Pretty Good Privacy) released in 1991. This provides secure AES and RSA implementations that been proven over time. Since we rely on the same open source implementation as proven actors like ProtonMail we can ensure that there isn’t any clandestinely built in back doors.
Our implementation relies on 4096 bits RSA keys even though RSA Laboratories estimate that 2048 bits should be sufficient until the year 2030. Since the intended use of our service is to mitigate an insecure user practice we want to make security a top priority.
End-to-end encryption
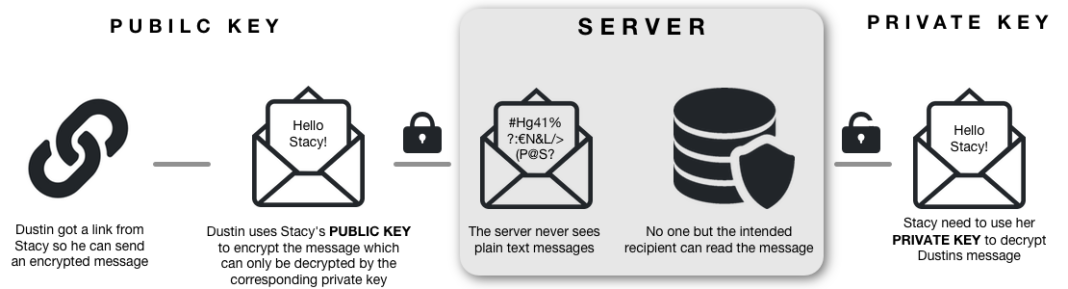
To protect our users and ourselves we never handle any unencrypted data. The message is encrypted on the sender side in such a way that only the intended recipient can decrypt it.
In addition to this encryption all communication between our users and our servers are secured with an additional layer of SSL 2048 bit encryption.
No access to user data
We don’t want any part of your data. The only part of the message that isn’t encrypted is the recipient address, without it it will be hard to deliver your message.
With the use of asymmetric encryption one key can only encrypt the message (public key). Once that is done only the private key with its password can decrypt the message. This way we can ensure that the message only reach the intended recipient.
Additional steps
In addition to all other security we don't transmit or store your password in any reversible form. Your credentials are salted and hashed on the client side as well on the server side. In addition to this it’s only transmitted over a 2048 bit SSL connection.
This is to prevent any useful information risking being leaked at any time. In the highly unlikely event of a credential leak the passwords will be extremely difficult to brute force.